- CPA to Cybersecurity
- Posts
- Break Into Cybersecurity GRC From Business
Break Into Cybersecurity GRC From Business
Last time I shared the foundational first steps I took to cross over from Finance to Cybersecurity Governance, Risk and Compliance:
Immersion in books, podcasts and blogs
Target a job, target an industry
Start framing up a 70-20-10 career experiences-relationships-education Career Development Plan
Today I'll pick up from there an unpack more next steps I took, that you might find helpful if you’re looking to break in. A backdrop for this conversation is some negative headlines over the past month:
Those are some pretty doom and gloom sounding headlines. But then bringing a more positive tone to this discussion is Forbes, when it says:
My viewpoint and experience is much more aligned to Forbes here. This channel CPA to Cybersecurity is not not about saying that accounting's bad and you need to get out it. I think accounting's great and lots of people in my network are living proof of that.
My thinking behind this channel is that there's a growing cyber crisis and cybersecurity skills shortage, that people from diverse backgrounds need to fill to protect our economy and national security. And I think other accounting and business people would be surprised like I was, at how many transferable skills they can bring to the team sport and business problem of cybersecurity.
Paraphrasing from the Forbes article:
While rooted in principles and structures, accounting surprisingly offers the flexibility to pivot, adapt and evolve in an unpredictable world. Beyond number crunching, it’s the language of business. It’s understanding the financial health of a venture, and bringing a holistic view to make decisions, to compete and win in the marketplace.
That's why my logo is a compass, because in both Finance and Cybersecurity GRC, you're a compass to help the businesses navigate to where it needs to go, and to reliably achieve objectives.
So if this sounds interesting to you and you want to take the leap, here's more steps from my journey that might be of help.
Last time I shared this Daniel Miessler article:
Today I have another one:
Miessler says unlike the military that takes time to train you and take you from zero to hero, commercial industry wants to hire people that can contribute from day one. They want People that already know how to do things.
He goes in to give some specific examples of what those things can be. And example #3 really jumped off the page at me, because it’s exactly what I did: I found a way to help prepare for and handle an audit.
Scenario: It’s Friday afternoon, and you just got told that Sarah, who normally handles the audit, is unexpectedly out of the office. The auditors show up Monday at 8 AM and you’re the new quarterback. Good luck.
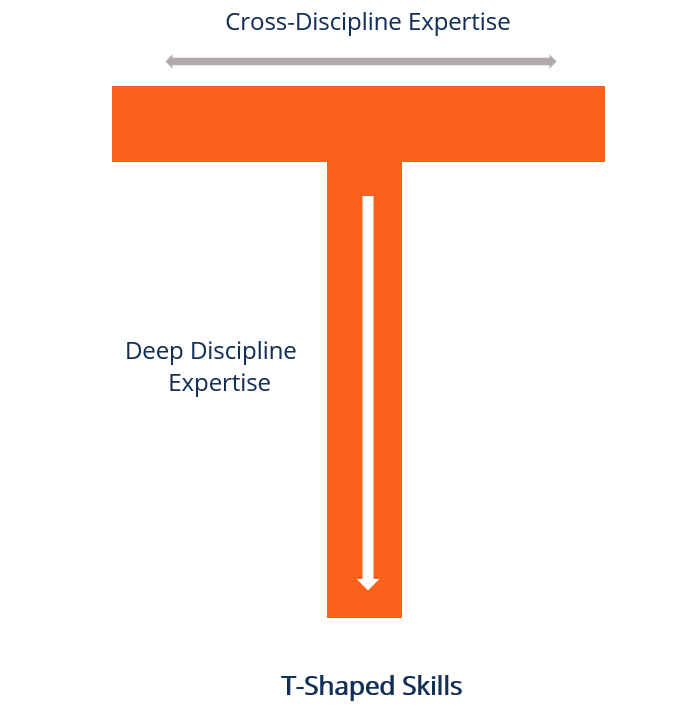
In every crisis lies the seed of opportunity. When I had to backfill the quarterback position of an external cybersecurity audit with zero notice, the concept of T-shaped skills is a key success factor that kept me afloat.
Cross discipline expertise if the top of the T and deep discipline expertise is a narrow but tall base. My depth of experience was heavy duty auditing, coming from the regulated Financial space, with a focus on IT general controls for financial systems: if you look at the NIST Cybersecurity Framework, this is primarily the PROTECT function with Identity & Access Management outcomes and controls.
My cross discipline expertise was shallow and broad, just book knowledge with limited hands on keyboard experience in other CSF control families: data security, protective technology, and then getting into the “right of boom” (post incident focused) functions of detect, respond and recover. These are much less of a focus in the integrity heavy Internal Control of Financial Reporting.
Being strong in one or a few narrow areas is a good strategy to add value from day one, because it puts you in a position to start making deposits in the reservoir of trust of the people around you. And in a new job you're making first impressions with them and establishing credibility.
So I latched on to Access Management controls where I knew the people, the tools, the processes and in fact had audited them to a heavier level in SOX than the scope of the audit I was thrown into. So for this small fraction of the work I could put points in the scoreboard for the team and didn't have to bug anyone with questions.
For networking controls and other areas out of my depth, however, I had a lot of questions, I was stuck and needed help. But it was much easier to ask my questions after having established credibility and having added some value independently.
So in your own journey of breaking in to a job you’re chasing after, I’d encourage you to think of ways you can do the same from your own vantage point. What are experiences and strengths you can build to draw from, to get that initial foothold and be able to add value from day one?
To wrap up I’ll share some podcasts relevant to this topic from Your Cyber Path:
Episode #60 Top 5 jobs to two-step your way into the cybersecurity industry. At 4 mins and 30 seconds in they talk about my story.
#58 How to get hired with no experience
And #47 How to use your transferrable skills
There’s lots more to unpack on this topic which I look forward to doing down the road. Don’t hesitate to add questions or provide feedback in the comments.
Thanks for reading and see you next time.