Search YouTube for GRC and you can’t miss Cyber Salih! I and thousands of others have found his setting certification BHAGs and diligently following through on them very inspiring.
We recently caught up on his channel to talk about:
4:41 - GRC Certification Roadmap
13:17 - Cert study approach and mindset
16:24 - Top GRC career resources
20:44 - Why GRC is awesome and underrated
31:33 - The GRC superpower
33:57 - NIST Cybersecurity Framework 2.0 Primer
38:37 - Where Compliance Can Go Wrong: Password Complexity Requirements
44:40 - AKYLADE Certified Cyber Resilience Fundamentals (A/CCRF) - Complete Training
Check it out for some great ideas to add to your career development plan.
Podcast Agenda
Setting and Achieving Certification Goals: Skills, Methods, Mindset
Podcast clip: Is the stigma around GRC true?
Cybersecurity is a team sport that needs diverse skills to advance its mission. If I were a L33t hacker with 10k hours understanding IT systems so well that I could break into them I’d think differently, but from my business background vantage point GRC is awesome and underrated!
Question for Salih:
🔲 Any to add, or any favourites from this list?
CISA Exam: How I passed and how you can too with this study technique
Your grit and determination to set a Big Hairy Audacious Goal (BHAG) and achieve it are admirable! I can relate to the texbook being dry (LOL!), and given that your advice on how to consume the course content is very smart.
Question for Salih:
🔲 How has CISA helped you in your job?
How to pass CISSP - 2024
Question for Salih:
🔲 Any top surprises you experienced, on or off my list?
CCSP - How to Pass the Exam

Hey you overcame significant obstacles and doubts even 1 week out and cleared this high bar! How inspiring - congratulations and kudos!
Question for Salih:
🔲 Has this one been helpful on the job?
Cyber 2nd Brain Resource Library
🧐 Content Recommendations
Blogs to read
Name | Link | Top 3? |
|---|---|---|
Schneier on Security | ✅ | |
Unsupervised Learning | 🔲 | |
CISO Series | 🔲 | |
Other? | ❓ |
People you should follow
Name | Link | Top 3? |
|---|---|---|
David Bombal | ✅ | |
Gerald Auger | ✅ | |
Ira Winkler | 🔲 | |
Other? | ❓ |
Note: all of these are awesome! Hard to shortlist a “Mount Rushmore.”
🤓 Education
📝 GRC Training
📋 Control Frameworks and Standards
SOC2 Trust Services Criteria (North America)
TISAX (Automotive, Europe)
🏅Certification Resources
CISSP
Resource | Link | In Cyber 2nd Brain? |
|---|---|---|
1. CISSP Subreddit | 🔲 | |
2. Official Study Guide (OSG) | ✅ | |
3. Cert Mike | 🔲 | |
4. Thor Pedersen | 🔲 | |
5. Gwen Bettwy Mock Exams | 🔲 | |
6. Destination Certification Mind Maps | ✅ | |
7. Pete Zerger: CISSP Exam Cram | 🔲 | |
8. Andrew Ramdayal: 50 Questions | 🔲 | |
9. Kelly Handerhan: Why you will pass the CISSP | ✅ | |
10. Prabh Nair | ✅ | |
11. Boson | ✅ |
Simply Cyber Academy
🐙 Career Resources
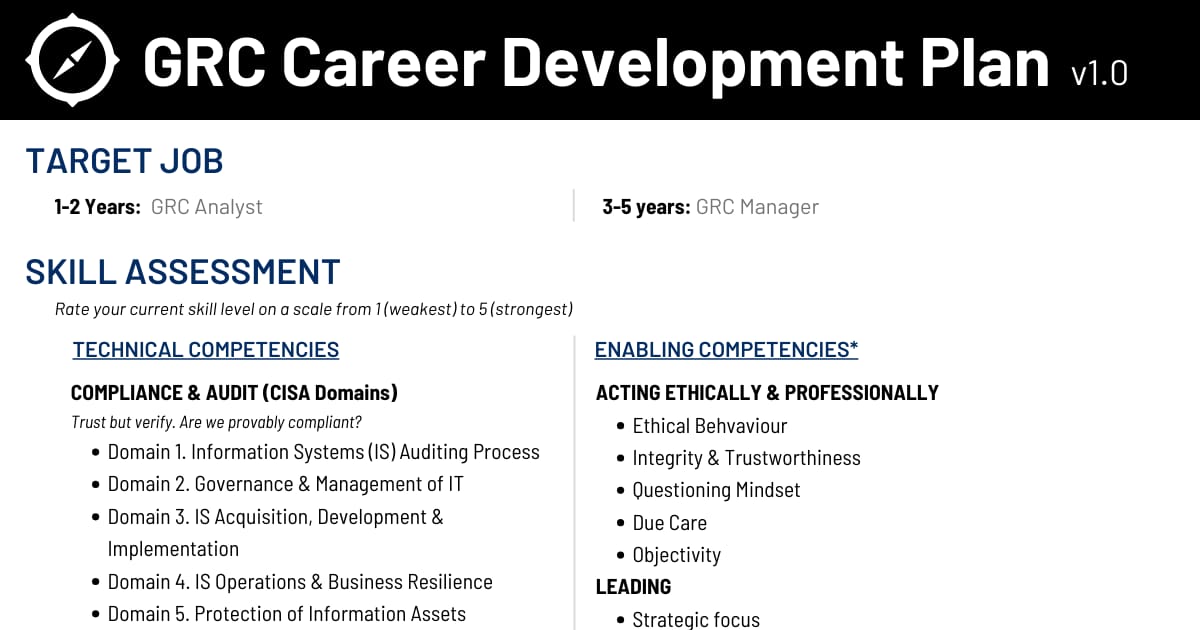
GRC Career Development Plan Template
Cyberseek.org (US)
Cyber Career Pathways Tool
SANS Templates
Their Acceptable Use Policy is really good at being end user focused
SOX
NIST Cybersecurity Framework 2.0
NIST CSF Origin
It is the policy of the United States to enhance the security and resilience of the Nation’s critical infrastructure and to maintain a cyber environment that encourages efficiency, innovation, and economic prosperity while promoting safety, security, business confidentiality, privacy, and civil liberties.
Recognized the growing threats to critical infrastructure and called for the development of a framework to enhance the cybersecurity posture of the United States.
It aimed to foster collaboration between the government and private sector, to improve the protection and resilience of critical infrastructure.
Established the requirements for NIST CSF
Applicability of the Cybersecurity Framework 🌎️
Bottom line why this framework is needed:
Cybersecurity risk continues to increase, with no signs of slowing down
Costs of cybersecurity risks continue to grow
Why? 🤔
The greatest threat that faces any of us today is the threat of complexity: Trillions of lines of code in billions of devices, with ubiquitous connectivity across the globe.
Characteristics of the Framework 📏
Voluntary Framework
The CSF is a foundational resource that may be adopted voluntarily and through governmental policies and mandates.
Flexible, Adaptive
The CSF describes desired outcomes that are intended to be understood by a broad audience, including executives, managers, and practitioners, regardless of their cybersecurity expertise. Because these outcomes are sector-, country-, and technology-neutral, they provide an organization with the flexibility needed to address their unique risks, technologies, and mission considerations.
Focus on Risk Instead of Controls
Organizations will continue to have unique risks — including different threats and vulnerabilities — and risk tolerances, as well as unique mission objectives and requirements. Thus, organizations’ approaches to managing risks and their implementations of the CSF will vary.
Focus on Risk Instead of Compliance
While compliance with regulations and standards is important, an organization’s goal is first to reduce risk, and to foster a risk-based mindset
Next, from that point compliance will naturally follow
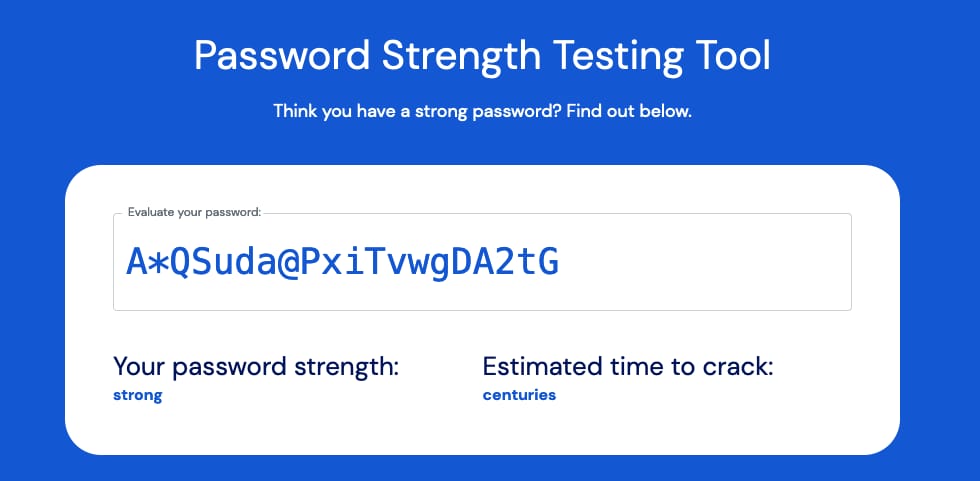
Where Compliance Can Go Wrong: Password Complexity Requirements
Is this password secure?
A*QSuda@PxiTvwgDA2tG


Other Options to Improve Authentication Security
Multi-Factor Authentication (MFA): This method requires users to provide two or more verification factors to gain access to a resource such as an application, online account, or a VPN. Common factors include something you know (password or PIN), something you have (a smartphone or hardware token), and something you are (biometrics: fingerprint scans, facial recognition, or iris scans).
Using Known Password Lists: Implementing checks against lists of known compromised passwords can prevent users from choosing passwords that are already exposed and easy to guess. This can be particularly effective in stopping common and repeated password-related vulnerabilities.
Time-based One-time Password (TOTP): This is an algorithm that generates a one-time password which is valid only for a short period of time, providing an additional layer of security by ensuring that the password is not reusable.
Geographic and IP Restrictions: Limiting access based on geographic location or IP addresses can help prevent unauthorized access from high-risk areas or unfamiliar sources.
Anomaly Detection and Login Monitoring: Tools that monitor login attempts and detect anomalies (like logins from new devices or locations) can trigger additional authentication requirements or alerts.
Facilitates Communication and Collaboration
When implementing the CSF, managers will focus on how to achieve risk targets through common services, controls, and collaboration, as expressed in the Target Profile and improved through the actions being tracked in the action plan (e.g., risk register, risk detail report, POA&M)
Holistic Cybersecurity Framework 🌐
Confidently navigate the complex landscape of cyber threats
Identify vulnerabilities ➡️ protect critical assets ➡️ detect potential breaches ➡️ respond effectively to incidents ➡️ recover swiftly from disruptions
Provides a high-level, strategic view of an orgnaization’s management lifecycle of any given cybersecurity risk
6 Functions ➡️ 22 Categories ➡️ 106 Subcategories


Cyber Resilience is Probably a Better Name than “Cybersecurity”
Term | Definition | So What? |
|---|---|---|
Cyber Resilience | An organization’s ability to withstand and adapt to cyber threats by implementing proactive measures, effectively responding to and recovering from cyber attacks or disruptions, and maintaining essential functions while minimizing damage. This encompasses a range of strategies, including robust security controls, regular vulnerability assessments, employee education on cybersecurity best practices, and the establishment of incident response plans. | Probably a better name than “Cybersecurity,” where secure seems narrowly PROTECT focused Think both left and right of boom “It’s not if, but when” “There’s two types of organizations” Be proactive to prevent or minimize impact of cyber incidents Also be able to quickly detect, isolate, restore and recover systems |
Intended Audience & Purpose of CSF 👥
Critical Infrastructure ⚙️
Term | Definition | So What |
|---|---|---|
Critical Infrastructure | “Any physical or virtual infrastructure that is considered so vital to the United States that its incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety, or any combination of these” - DHS | The Department of Homeland Security (DHS) lists 16 Critical Infrastructure sectors |
Chemical - Organizations and companies that manufacture, store, use, and transport potentially dangerous chemicals used by other critical infrastructure sectors
Commercial Facilities - Buildings, facilities, and spaces used for commercial purposes, including retail, entertainment, and hospitality
Communications - Networks, systems, and assets involved in providing communication services, including broadcasting, telecommunications, and internet service providers
Critical Manufacturing - Facilities and processes involved in the production of essential goods, such as metals, machinery, transportation equipment, and pharmaceuticals
Dams - Structures, systems, and resources related to dam operations and water control, including hydroelectric power generation .
Defense Industrial Base - Companies and assets involved in the research, development, production, and maintenance of defense-related equipment, systems, and services
Emergency Services - Agencies, organizations, and personnel responsible for emergency management, firefighting, medical services, and public safety
Energy - Resources, systems, and infrastructure involved in the production, transmission, and distribution of energy, including electricity, oil, and natural gas
Financial Services - Institutions and systems providing financial services, including banking, insurance, investment, and payment systems
Food and Agriculture Sector - Facilities, systems, and resources related to the production, processing, and distribution of food, beverages, and agricultural products
Government Facilities - Buildings, offices, and structures used by federal, state, local, tribal, and territorial governments for administrative and public services
Healthcare and Public Health - Facilities, personnel, and networks involved in providing healthcare services, medical research, and public health support
Information Technology - Systems, networks, and infrastructure used for information processing, storage, and communication, including software development and cybersecurity
Nuclear Reactors, Materials, and Waste - Facilities, processes, and materials associated with nuclear power generation, research, and waste management
Transportation Systems - Infrastructure, networks, and assets involved in the movement of people and goods, including aviation, maritime, rail, and road transportation
Water and Wastewater Systems - Facilities, systems, and resources responsible for providing drinking water and managing wastewater treatment and disposal
Valuable beyond Critical Infrastructure
Non-Critical Verticals | CSF Benefits |
|---|---|
Retail | Protect their customer’s data, secure the company’s online transactions, and manage their supply chain vulnerabilities |
Manufacturing | Address industrial control system security and intellectual property protection and to help secure product development |
CSF is a series of best practices and guidelines and not a compliance standard that must be strictly adhered to
It can be scaled up or down
Only 32 pages long in version 2.0!
Concise and relatively quick to implement
BUT – official NIST documents tell you what to do, without telling you how to do it
That is why A/CCRF and A/CCRP are important to your career growth and progression!
Purpose

CSF helps organizations:
Describe current cybersecurity posture
Describe target state for cybersecurity
Identify and prioritize opportunities for improvement
Assess progress toward the target state
Communicate among internal and external stakeholders